Welcome to the CTF writeup page!
As much as it pains me to do this, I figure it will be easier to just link people this page so they can see writeups easily without having to find them. This will be the ONLY exception to my "Only 1 page full of everything" rule. If you would like to visit the main page please click
Be warned, it is not at all as tidy as this one.
Writeups!
NULLCON GOA 2025
(2/2/25)Flag checker
I first used DIE.exe to check the binary was decompilable.
Then, using Ghidra I examine the functions.
FUN_00101318 catches my eye, and in turn links to FUN_0010127a
FUN_00101318
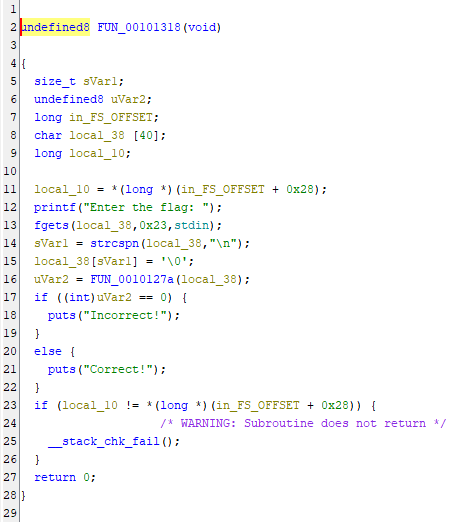
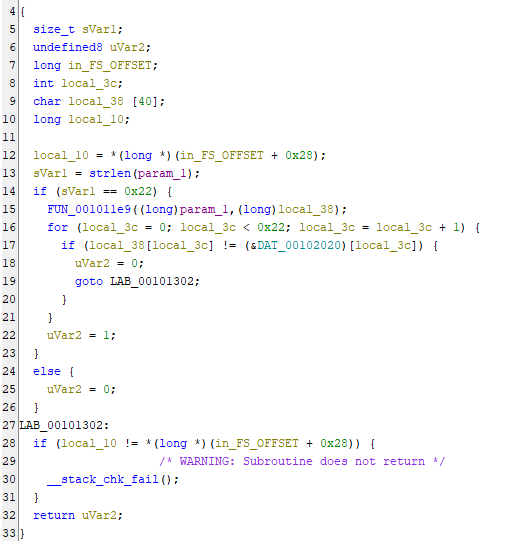
Checking FUN_0010127a reveals that it takes encoded bytes from DAT_00102020 and further links to FUN_001011e9
FUN_0010127a
DAT_00102020
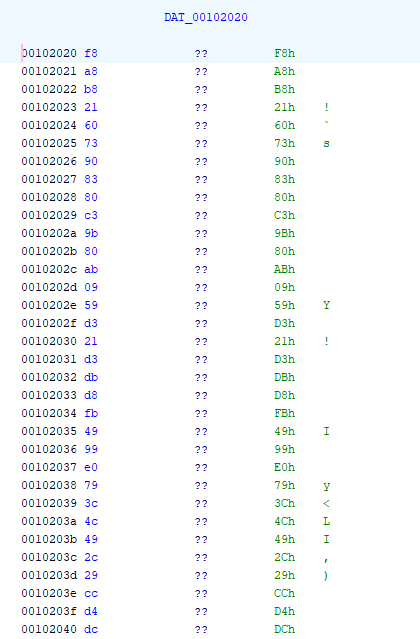
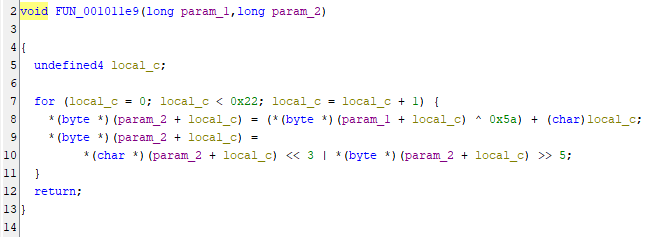
FUN_001011e9 is reversible, allowing us to input the encoded bytes from DAT_00102020 to create the flag
FUN_001011e9
Python script
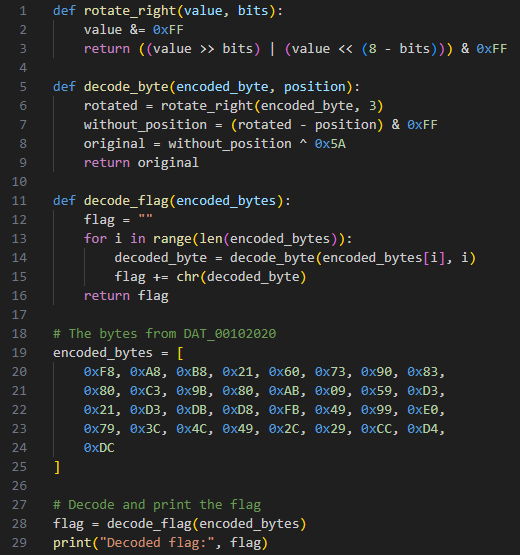
ENO{R3V3R53_3NG1N33R1NG_M45T3R!!!}
(2/2/25)Scrambled
We are given the following code and output:
result: 1e78197567121966196e757e1f69781e1e1f7e736d6d1f75196e75191b646e196f6465510b0b0b57
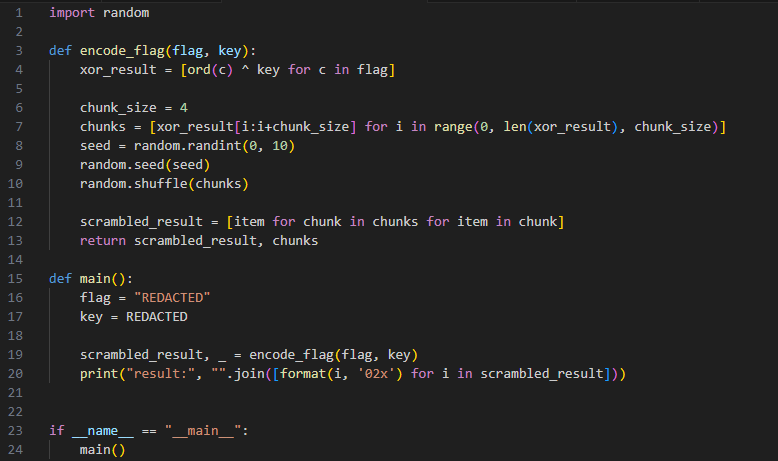
We can then reverse this code and run it, examining the results and looking for a key
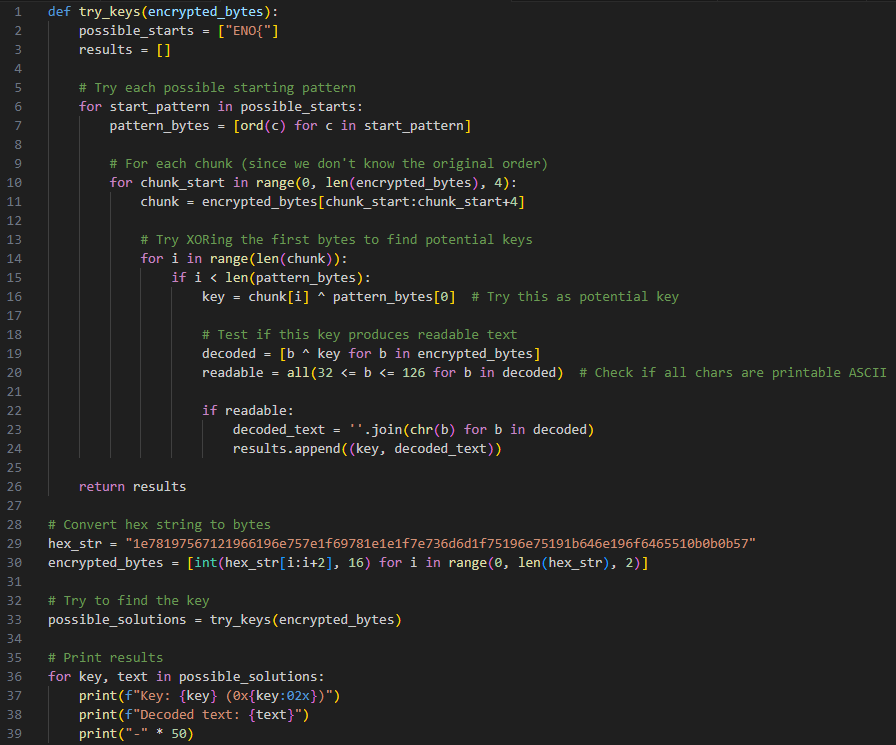
This decoded text looks suspiciously like a flag
Key: 42 (0x2a)
Decoded text: 4R3_M83L3D_T5CR445TYGG5_3D_31ND3ENO{!!!}
We can then.... manually.... rearrange..... this key to get
ENO{5CR4M83L3D_3GG5_4R3_1ND33D_T45TY!!!}
LACTF 2025
(8/2/25)javascryption
You wake up alone in a dark cabin, held captive by a bushy-haired man demanding you submit a "flag" to leave. Can you escape?
since there is js in title we check the website's debugger tab and find the following js:
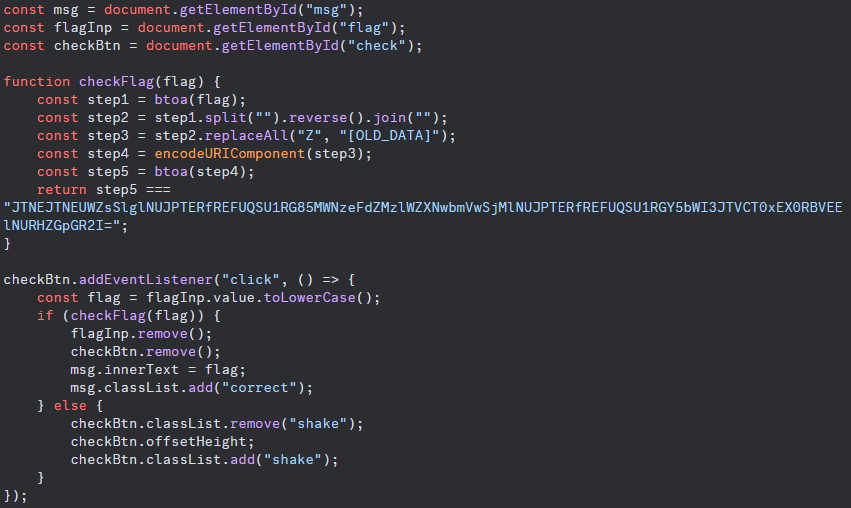
this challenge is nicely laid out in front of us, so lets work backwards through the steps.
"JTNEJTNEUWZsSlglNUJPTERfREFUQSU1RG85MWNzeFdZMzlWZXNwbmVwSj
MlNUJPTERfREFUQSU1RGY5bWI3JTVCT0xEX0RBVEElNURHZGpGR2I="
is the resulting string after the 5 steps defined in the code.
Step 5 asks us to convert the string to base 64, so we translate it from base64.
%3D%3DQflJX%5BOLD_DATA%5Do91csxWY39Vespne
pJ3%5BOLD_DATA%5Df9mb7%5BOLD_DATA%5DGdjFGb
step 4 converts parts of the string into url encoding, so we convert it back to normal
==QflJX[OLD_DATA]o91csxWY39VespnepJ3[OLD_DATA]f9mb7[OLD_DATA]GdjFGb
step 3 converts all capital "Z"s to "[OLD_DATA]"
==QflJXZo91csxWY39VespnepJ3Zf9mb7ZGdjFGb
step 2 reverses all the characters
bGFjdGZ7bm9fZ3JpenpseV93YWxsc19oZXJlfQ==
step 1 converts to base 64. So,,,,
lactf{no_grizzly_walls_here}
(8/2/25)patricks-paraflag
I was going to give you the flag, but I dropped it into my parabox, and when I pulled it back out, it got all scrambled up! Can you recover the flag?
time for todays episode of Put That File In DIE.exe And Then In Ghidra !!!!
Put the file in DIE.exe to make sure we can decompile the file
Then put the file in Ghidra to decompile
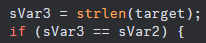
in main we discover that this function checks to see if the inputted string is the same length as the target
in main we discover that this function checks to see if the inputted string is the same length as the target
if it is, the "paradoxification" process begins
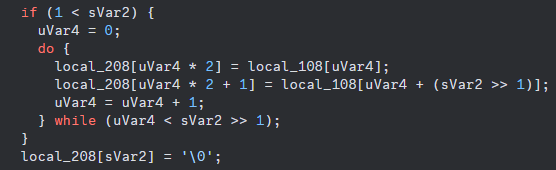
basically, if the string is longer than 2 characters a new string will be created by taking half the second half of the string and placing it after each letter in the first half of the string (ABCDEF -> ADBECF)
we can see from earlier that the target is
l_alcotsft{_tihne__ifnlfaign_igtoyt}
you can either write a program or rearrange this by hand, resulting in the following:
part 1 : lactf{the_infinity}
part 2 : _lost_in_flag_got
finally, rearranging gives us
lactf{the_flag_got_lost_in_infinity}









